Sunday, August 28, 2005
VON Magazine on IMS and ENUM
Let’s not get carried away. The optimistic view of IMS (IP-based Multimedia Sub-system, the future common service architecture for both wireless and wireline communications) predicts service delivery in Q1 2006 and SIP-compliant devices will be needed. The other view is for an appearance in 2007/08 along with a prediction of problems with the new cell phones (see the sidebar entitled, “Shades of Gray”). Only time will tell who is right and both views are obviously driven by agendas, but the vibes were very positive in Stockholm.
I have stated my view on IMS here many times and I understand that the VON Magazine cannot fully argue against the main customers and sponsors of the VON Conferences, so they are citing them instead, which is sufficient for a give-away, e.g.:
Brough Turner, CTO at NMS Communications: “IMS is the intelligent network (IN) of our decade. Yes, IMS’s separation of signaling and transport is more efficient, and the potential access to new application development environments may help… IN was important (think mobile roaming and prepaid) and IMS will be important, but let’s not get carried away by the hype… IMS comes in several revisions, some not fully baked; additional revisions will emerge over the next decade.”
So IMS = IN, now it is official. I expect a comment from David S. Isenberg on this statement in the next issue of VON Magazine ;-)
Bertrand Chauvet, international business development director, Netcentrex, comes at it from an NGN perspective: “What is really good with IMS as a specification, what really makes the difference with the legacy IN, is the simple recognition that with VoIP there’s no tromboning [traffic making forwards and backwards trips to the same location]. This architectural change is extremely important and it will have a big impact on the NGN.”
Aha, so there IS a difference between IMS and IN. This statement is really a nice one -
IMS is here to prevent tromboning!
There is no technical reason for tromboning in GSM since 1990, yet there is still tromboning. And as far as I know, the IMS version to be implemented in 3GPP now will tunnel from the visited network to the home network. In my naivity I call this tromboning also.
Bob Emmerson himself seems to be not so happy what he is citing and saying on page 28, because already on page 36 in his second feature on Euro Innovation - Triple play, guaranteed seamless handovers & pseudo-wires he is stating prominently:
The way ahead:
Telephony is becoming a free application like email and IM; i.e., it will be part of a broadband service bundle. There are around 40 million broadband lines in the EU, up 70% from last year, and carriers have excess DSL capacity.
The whole article is not mentioning IMS at all.
BTW, also Professor Henning Schulzrinne, in the excellent interview in the VON Magazine July issue is not mentioning IMS with one single word.
Last but not least, the July issue of VON Magazine has also an interesting article on ENUM - Great idea but ... from Richard Grigonis. Richard first gives a well researched overview and introduction on ENUM, then from an interview with Tom McGarry, Neustar, an overview on the current (May 2005) status on User, Private and Carrier ENUM. In the last section titled: Today Austria, Next Year the US? he is citing from my presentation and what I said at VON Europe 2005.
As we all know, things have moved forward in the meantime in Paris, but his last sentence is still correct:
So, ENUM isn't quite ready for world conquest as yet. Let's see what next year brings.
Thursday, August 25, 2005
Callback - Portblocking - JAJAH - Callback again
How Callback Paved the Way for Internet Telephony
It is basically the story of Martin Varsavsky and Viatel and goes like this:
Martin Varsavsky, a refugee from Argentina in 1977, bought the Boulder (Colorado) Holiday Inn in 1987. He noticed that the telephone system was the most robust source of profits in the hotel. He was impressed. Rather than try to bring the rest of the hotel’s profitability up, he focused on making the hotel’s strongest business even stronger.
In 1990 it cost over five dollars a minute to call the US from Argentina. In the US it was another story. Long distance competition was booming as a result of the Bell System breakup. Calls to Argentina from the US cost as little as a dollar a minute. Varsavsky seized the situation. He used his contacts in Argentina to recruit customers. He used the Boulder Holiday Inn’s PBX to do the callback. He charged three dollars a minute; he was making money and his Argentine customers were saving – the only loser was Telintar, the former incumbent in Argentina (dissolved in 1998) .... Varsavsky took his callback venture, Viatel, to Wall Street, where George Soros became the first investor.
Argentine monopoly Telintar was not happy with Viatel’s success. Telintar tried to put Viatel out of business by blocking calls to the particular US area code and exchange of Viatel’s platform. Viatel retaliated by moving its platform to the same exchange that served the Argentine Embassy in Washington, DC; thus, if Telintar exchange-blocked Viatel, it’d leave its own embassy unable to accept calls from the home country.
So this was IMHO the first try of "port" blocking and one way to deal with this - e.g. use a port that cannot be blocked ;-)
David concludes in his last paragraph - Callback's rise and fall - that ...
... Callback smoothed the way for Internet Telephony by introducing monopoly telcos to the idea of uninvited competitors who won’t go away. Varsavsky believes that callback did more; it showed that, “tools that can dismantle techno-censorship,” could undermine established giants....
... but that the hey-days of callback are over. I agree, because all these services are living on arbitrage, using the asymmetrical rates introduced by weird, over-complicated and wrong tariff-models and such things are normally very short lived.
OK, done.
One hour later I got news that JAJAH is offering call-back services to VoIP and PSTN from any mobile phone. Huh? What the heck is Jajah?
The description goes like this: after subscribing for the service, you browse to the webpage mobile.jajah.com on your mobile phone, authenticate with your userid and password, enter the phone number of your mobile and then the number you want to call.
This is basically nothing new, there is a bunch of such arbitrage services already available, e.g. hop, oneroam, globalSIM, sim4travel, etc.
I was only getting curious by the following entry pointing to engadget:
Jajah Mobile promises VoIP from your cellphone
It’s not officially launched, but Speedblog (Italian) got their hands on a beta version of some new software called Jajah Mobile, which lets you do VoIP calls via a web browser on your cellphone. They tested it with a Nokia 6630 and the Opera browser and while it was buggy for reaching landlines in their home country of Italy, it seems like it could be a pretty reasonably-priced solution for placing international calls from your mobile. Calls to other Jajah users and SIP phone numbers are free, while calls to landlines and non-Jajah cellphones incur tariffs based on location. The first official version of the software should hit sometime this week.
Calls to SIP phone numbers? Hey? What is this?
So I had to do some beta-testing again ;-)
I downloaded the client and although it needs some work in user interface and the sound quality is normal (obviously no GIPS yet), it is a gem and has the potential to stay my prime client:
Of course you can call other users of the jajah community, BUT in ADDITION you can call:
- any E.164 number,
- any SIP URI !
- any Skype name ! (ala pulver communicator)
- it even supports IAX !
As I said, there is still some work to do, e.g. showing your Skype Buddies automatically in the buddy list like the pulver communicator, adding a better sound engine and codecs, improving the user interface. There is also the problem that you cannot access Skype directly as long as the jajah client is running.
The rates are a bit higher than Skype, but comparable. Somewhat disappointing for me is that although they have rates for the Austrian VoIP Numbers +43720 and +43780 (normally it is the other way round - the mobile operators always claim that they first have to define the rates - for all packages - and this takes years, because it involves tons of product managers and I think they have lost themselves the control how many packages they allready have - but I get carried away here ;-).
... but the rates are very high (0,3539$/min), same like to Mobile 3G (Hutchinson), compared to 0,1934$/min to mobile A1, 0,0173$/min to Vienna and 0,0121$/min to the US - but this does not matter, you cannot call these numbers anyway.
So there are ups and downs, but much lee-way for improvements.
The only thing never worked for me was starting the call-back sequence on my mobile phone direct, because I am obviosly too stupid to enter my alphanumeric password on a mobile key-pad. But using the web-page from my laptop, it worked like a charm. And if you enter the wrong password, you have to enter your UserID (which is your e-mail address (alpha again) and the mobile number (in alpha mode!) again. Until they do not find another way to trigger the call-back from the mobile phone web-page, I am not able to use this feature, sorry.
Wednesday, August 24, 2005
Lower Austria Special
Me Too Two
Anyway, I scanned the following entries from my fellow bloggers and made up my mind (in alphabetical order as they appear in my newreader):
Skype vs. Google Talk
Google Talk
Google Talk
Google Talk
Google Walks into Telephony with Talk
Google's Jabber is alive, works with iChat AV
Google IM & VoIP - Google Talk is Live
Google Talk Skype Killer?
Google Talk Up and Running
Why Skype needs Google
Google Talk Launches: May the Federation(s) Begin
Google’s Own Client for Google Talk, and Mac Google Talk Info
Google Talk Test Drive
Google IM Now Out
GizmoProject To Link With GoogleTalk
I have not much to add to these comments.
Google talk is NOT SIP (yet), maybe in later versions as Andy points out.
I finally agree with Om, who tried it out:
Still, an hour or so later, I am wondering why I need another Voice-over-IM client, given that I don’t use the ones that I have right now as much.So I saved an hour or so ;-)
UPDATE:
And the discussion is going on and on:
Google Talk(s), But What Does it Say?
Enter the dragon
More about Google Talk
Google Talk: Another Quick Look
Google VoIP Day 2: Feeling a little let down
Google Talk Polygamy for multiple identities
Google Talk supports SIP, what does Skype do now?
Observations About Google From A Reader
Of course this hype is precisely monitored and measured by Skype Journal:
Google Talk Goes Blogosperically Viral
as it is shown here:
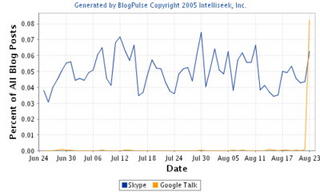
Me Too - Google Talk - Me Too
I'm a bit disappointed, because most other applications launched by Google are quite impressive, e.g. Picasa, Google Desktop, Google Earth. Google Talk looks to me like a quick botch-up just also to have a voice client.
I have expected more from Google than a Me Too.
Saturday, August 20, 2005
The New Dawn of Vonage
Friday, August 19, 2005
Washington is not Hollywood - The Empire strikes back
Scott Bradner is complaining and this is also referenced by James and David.
David has a very good post and I copy it here completely, because I fully agree and have nothing to add. It also contains the links to the important documents:
A number of incredibly sweeping rule changes that could change the way we use the Inernet forever are in motion. This is all happening with very little fanfare. Where is the outrage over the latest kick in the collective balls of consumers?
As Scott Bradner put it in his 08/15/05 post on the recent FCC actions:
So now we know that the FCC's priorities are, in order: 1) protect incumbent carriers, 2) give law enforcement more than it needs and a distant 3) pretend to be concerned about the customer.
The recent FCC rulings essentially say that he who owns the access link may control what flows over that link. This means those providing the access link will decide what applications we run. And guess what? Those that own the link consider that we (their customers) are ripping them off every time we use Google to find a website, because they aren't getting a piece of that action. So what does that tell you about the Internet we will "enjoy" in the years to come, as the incuments and cable companies get their way?
The FCC has made a lot of noise about the so called "four freedoms" which include being able to access Internet content, run whatever applications you want and having competition among providers. But these principles are apparently not important enough to be made made into law or even an FCC regulation. And Scott Bradner points out that even when stated as simply guiding principles (rather than rules or regulations) the FCC waters them down to "worthlessness":
For example, you can run any application as long as law enforcement says you can. For some of the law enforcement people I've talked to that would mean you could not use a VPN back to the office to read your confidential corporate e-mail. In addition, all four principles are subservient to "reasonable network management," meaning that an ISP could say I can't manage my network if you run that application or access that content.
This is a war of attrition, to which the incumbents excel... and they are winning. It took them almost 10 years, but they have finallly won the line sharing battle and achieved the utter destruction of the 1996 Communications Act.
The incumbent LECs and their supposed competition (the cable companies), will continue to wage this war of attrition against the "four freedoms" and of course the FCC, with the help of DOJ and the Supreme Court, will comply. Don't kid yourself; no one speaks for the consumer. The FCC likes to make statements about how "consumers would never stand for application blocking by access providers." Apparently consumers will stand for it. Besides, what choice will they have?
Intelligent Design?
The Austrian cardinal Schoenborn wanted to be interviewed once in a life by the "New York Times" and to get some attention he picked a very hot topic in the US, at least according to the "Scientific American": the battle between Creationists and Darwinists. Some say that this action was triggered by his old friend PapaRazzi himself. He had to do this in the US, because in European newspapers this issue would not even make it on page 20 under topic miscellaneous.
Of course he offered a compromise by talking about an "Intelligent Design" controlling the chances of the evolution. Ok, this may be his opinon, I had only a problem with his second statement: that any intelligent person can see this. This from a roman-catholic priest forced by dogma to believe the wierdest and most contradictory things. It should also be mentioned that this statement was even rejected by George Coyne SJ from the Vatican Conservatory.
But what about the "Intelligent Design" idea in general?
Intelligent Design suggests that the universe is so impressive to us humans that someone much brighter than us must have created it. But it doesn't take much to be superhuman. Always remember that humans are very stupid and easily impressed.
It makes more sense to say that, far from showing signs of intelligence, the universe is a very badly planned entity. Almost all of it is empty space, and what little matter there is is useless. If I where an intelligent designer and I'd made the universe, I wouldn't mention it on my CV.
So is the universe an "Unintelligent Design" or is it a "Bad Design"?
One could say that especially life is unnecessary complicated and is using complex processes. Scientists like complexity and are impressed and some say that there must be an intelligence at work.
But one could also argue the other way round - that IF there was any intelligent designer at work, he would have cleaned up these complicated processes years ago and streamlined everything.
Complexity is always a feature of "Bad Design" - KISS
Ok, this entry should not be taken too serious.
And no, I am not talking about SIP, NGN and IMS ;-)
Allahu Akbar
The issue I do not understand with these bombings and especially with suicide bombers is the reaction of the religious leaders, in this case the muslims. Ok, there are always the "useful idiots" within the western society saying they understand at least the motivation of these people blowing up themselves and/or some innocent by-standers- basically the same people supporting Che, Fidel, Stalin and Ho Chi Min. I don't.
But the muslim religious leaders should reject the basic idea of such activities simply as blasphemy. Up to now I did not hear this.
All monotheistic religions (Christians, Muslims and Jews) consider God as allmighty or omnipotent. Some may say Christianity is not strictly monotheistic, featuring three gods and a goddess (Mary) and some Jews may have doubts about God being omnipotent as demonstrated in this story:
A rabbi wants to explain his pupils what allmightyness means: "God is so allmighty that he can create a rock so big that nobody can lift it". Since his pupils did not seem to be very impressed, he added: "He may even create a rock so heavy that even he himself cannot lift it". The pupils where impressed now, but the rabbi thought to himself: "But where is he then allmighty?"
But for the muslims there is no doubt and they have to state this at least five time a day in the prayer. So if anybody even thinks that this allmighty god needs the help of a brain-damaged youth to make a point, I would consider the idea alone as blasphemy.
Why brain-damaged? Because anybody having his senses together and being approached by somebody promising immediate salvation and going non-stop to paradise would answer: "If you consider this as such a good idea, why don't you do it yourself in the first place?"
Friday, August 12, 2005
Binge-drinking
There is an increasing resistance against, because some say the British drinking habits cannot be compared with the adult drinking habits in (Southern) Continental Europe, because here drinking is always connected with food. The Brits drink without food and cannot stop until last orders are called. There is also this habit that in a group of people everybody has at least to pay one round. Naive Non-Brits try to argue: "If this is a large group, you cannot drink so much". The simple answer given is always: " Maybe, but at least we try".
On the other hand the papers say the Brits start to spoil the French already, some mention "Wine Bars Anglais" to be seen in Paris, where people can drink wine without having a meal. Knowing the French, I personally think that a Frenchman would rather change to the opposite side of the street than entering a "Wine Bar Anglais".
I found an excellent counter argument in yesterdays "The Independent":
"The Governement is extending opening hours so people will drink more, fall over and not commit crime."
Sounds reasonable.
Monday, August 08, 2005
For Austrians only
Now the European Commission changed this the other way round: German must be treated the same way like Austrians. As a result, the Austrian universities, especially for medical science are overrun by Germans not getting a place at a German university because of the German "Numerus Clausus". This is BTW one of the reasons why the population is so enthusiastic about the EU.
The solution: introduction of an aptitude test, the "Numerus Austriacus Medicinalis", confronting Austrians and Germans with completely identical questions out of the applied everyday medical life. Since the students need to know this in their later practice anyway, a slight Austrian language touch must be allowed.
Fuer unsere deutschen Freunde: Der Eignungtest ist natuerlich fairerweise in Hochdeutsch (Die dezente Heranziehung minimal identitätsstiftender Austriazismen muss dabei erlaubt sein.)
Die Eignungstestfragen:
1. Ein wamperter Tschecherant steht blunznfett mit einer Eitrigen auf einem Fensterbankl im Mezzanin. Sind notfallmedizinische Maßnahmen aus ärztlicher Sicht angezeigt?
2. Darf raunzendes Pflegepersonal scheanglnden Tachinierern ein Jaukerl geben, während diese bueseln?
3. Sie besuchen ein Wiener Kaffeehaus und geben sich als Medizinstudent(in) im 1. Semester zu erkennen. Die korrekte Anrede durch den Ober lautet:
a. Herr/Frau Metzgerlehrling
b. Awezahrer & BAföG-Zutzler
c. Herr/Frau Doktor oder gleich Herr/Frau Medizinalrat.
4. Ein Zniachtl von einem Patienten verkutzt sich: Seine Birne sieht plötzlich aus wie ein Paradeiser. Ist es korrekt, die Birne des Patienten einzufatschen, sollte man ihm ein Pulverl geben oder reicht es, wenn er ein gutes Papperl bekommt?
5. Wären die obgenannten Methoden geeigneter, wenn unser Patient statt dem Friedhofsjodler ein Schlagerl gehabt hätte?
7. Muss jemand mit marodem Beuschl, der fesch weitertschickt, den Löffel abgeben?
8. Ein schaasaugerter Patient reißt einen Stern. Nach dem Buserer hat er einen Dippel. Er hat einen ziemlichen Fetzen. Er speibt sich in der Notaufnahme an. Kann zum Entfernen des Gespiebenen auch der Fetzen des Patienten verwendet werden? Wenn nein - warum nicht?
9. Ein verwoadaglter, nicht assekurierter Straßenmusiker kommt mit der Quetschn am Arm ins Spital. Die Quetschn wird nicht behandelt. Kann er mit der Quetschn am nächsten Tag wieder musizieren?
10. Ein Chirurg darf nicht tramhappert sein, sondern muß bei seiner Hackn aufpassen wie ein:
a. Schuhmacher(in)
b. Engelmacher(in)
c. Haftelmacher(in)
11. Unterm Bett eines Patienten liegt ein Lurch. Was tun Sie?
a. Lassen sie die Station evakuieren und verständigen das amphibische Institut.
b. Sie versuchen mit Hilfe des Patienten den Lurch zu fangen.
c. Sie rufen den Reinigungsdienst und lassen auch gleich den Nachtscheam ausleeren.
Zugang zum Medizinstudium in Oesterreich nur mit mindestens 10 richtigen Antworten.
Aus den "Salzburger Nachrichten"
Austrians the better Germans?
Austria Shows Sick Cousin the Way Ahead
The story starts with:
We have become used to reading about the dire state of the German economy. Unemployment soars, incomes flag, the birthrate declines, and the government stumbles toward an almost certain electoral defeat.That's why it comes as a surprise to read about an economy of a German-speaking country that is doing pretty well.
In a quiet way, Austria has been consistently outperforming its close cultural and linguistic neighbor. There are lessons in that about where Germany itself went wrong, and about its prospects for transforming itself in the years ahead.
... explains some of the major highlights of the differences and ends with:
The lesson for the bigger of the two German-speaking economies is simple. If Austria can prosper, so can Germany. Austria's big cousin just needs to find the will power to change.
This is obviously a hint to the Germans NOT to re-elect the Red-Green coalition a third time (how stupid one can get?) in September 2005. Interestingly the Red-Green opposition in Austria is blaming the conservative government to be complete idiots and/or morons. This is BTW the same conservative government that was blackballed by all other 14 EU-governments in 2001, basically the same governments now driving Europe against the wall.
On the other hand, this success is nothing new: see Five Decades of Success - Austria’s Economic Rise within the OECD since 1950 (pdf), Anton Kausel
As a result one could come to another explanation: the influence of a democratic government on the ecomomy of a country is (luckily?) neglectible, it is basically the people itself. So the impact of the outcome of elections to the econmic success of a country is the same as pushing the close door button in an elevator. This may even be a comfort button like in the elevator of the Meridian in Paris (not connected to anything, because the door is closing anyway).
Sunday, August 07, 2005
S4 - The Systems Standards Stockholm Syndrome
See also the Wikedpedia glossary from Martin below:
IMS. Internet Monetisation System. A minor adjustment to Internet Protocol to add a “price” field to packet headers. Earlier versions referred to Innovation Minimisation System. This usage is now deprecated. (Expected release Q2 2012, not available in all markets, check with your service provider in case of sudden loss of unmediated connectivity.)It is so true that I have to cite it completely (bold emphasis added):
The “Stockholm Syndrome” describes the behavior of some hostages. The “System Standards Stockholm Syndrome” (S4) describes the behavior of system standards participants who, over time, become addicted to technology complexity and hostages of group thinking.
Although the original name derives from a 1973 hostage incident in Stockholm, Sweden, the expanded name and its acronym, S4, applies specifically to systems standards participants who suffer repeated exposure to cult dogma contained in working group documents and plenary presentations. By the end of a week in captivity, Stockholm Syndrome victims may resist rescue attempts, and afterwards refuse to testify against their captors. In system standards settings, S4 victims have been known to resist innovation and even refuse to compete against their competitors.
Recent incidents involving too much system standards attendance have resulted in people being captured by radical ITU-like factions known as the 3GPP or 3GPP2.
I have to add of course ETSI TISPAN and it seems that the syndrome is also spreading into IETF, especially to SIP and SIPPING.
The victims evolve to unwitting accomplices of the group as they become immune to the frustration of slow plodding progress, thrive on complexity and slowly turn a blind eye to innovative ideas. When released, they continue to support their captors in filtering out disruptive innovation, and have been known to even assist in the creation and perpetuation of bureaucracy.
Years after intervention and detoxification, they often regret their system standards involvement. Today, I am afraid that S4 cases occur regularly at system standards organizations.
What causes S4? Captives identify with their captors initially as a defensive mechanism, out of fear of intellectual challenges. Small acts of kindness by the captors, such as granting a secretarial role (often called a “chair”) to a captive in a working group are magnified, since finding perspective in a systems standards meeting, just like a hostage situation, is by definition impossible. Rescue attempts are problematic, since the captive could become mentally incapacitated by suddenly being removed from a codependent environment.
It’s important to note that these symptoms occur under tremendous emotional and/or physical duress due to lack of sleep and abusive travel schedules. Victims of S4 often report the application of other classic “cult programming” techniques, including:
- The encouraged ingestion of mind-altering substances. Under the influence of alcohol, complex systems standards can seem simpler and almost rational.
- “Love-fests” in which victims are surrounded by cultists who feign an interest in them and their ideas. For example, “We’d love you to tell us how the Internet would solve this problem!”
- Peer pressure. Professional, well-dressed individuals with standing in the systems standards bureaucracy often become more attractive to the captive than the casual sorts commonly seen at IETF meetings.
Back in their home environments, S4 victims may justify continuing their bureaucratic behavior, often rationalizing and defending their system standard tormentors, even to the extent of projecting undesirable system standard attributes onto component standards bodies. For example, some have been heard murmuring, “The IETF is no picnic and even more bureaucratic than 3GPP or the ITU,” or, “The IEEE is hugely political.” (For more serious discussion of component and system standards models, see “Closed Architectures, Closed Systems And Closed Minds,” BCR, October 2004.)
On a serious note, the ITU’s IMS (IP Multimedia Subsystem) shows every sign of becoming the latest example of systems standards groupthink. Its concepts are more than seven years old and still not deployed, while its release train lengthens with functional expansions and change requests. Even a cursory inspection of the IMS architecture reveals the complexity that results from:
- decomposing every device into its most granular functions and linkages; and
- tracking and controlling every user’s behavior and related billing.
The proliferation of boxes and protocols, and the state management required for data tracking and control, lead to cognitive overload but little end user value.
It is remarkable that engineers who attend system standards bodies and use modern Internet- and Ethernet-based tools don’t apply to their work some of the simplicity learned from years of Internet and Ethernet success: to build only what is good enough, and as simply as possible.
The lengthy and detailed effort that characterizes systems standards sometimes produces a bit of success, as the 18 years of GSM development (1980 to 1998) demonstrate. Yet such successes are highly optimized, very complex and thus difficult to upgrade, modify and extend.
Email is a great example. More than 15 years of popular email usage have passed, and today email on wireless is just beginning to approach significant usage by ordinary people.
The IMS is being hyped as a way to reduce the difficulty of integrating new services, when in fact it may do just the opposite. IMS could well inhibit new services integration due to its complexity and related impacts on cost, scalability, reliability, OAM, etc.
Not to mention the sad S4 effects on all those engineers participating in IMS-related standards efforts.
Here the Wikedpedia glossary from Martin Geddes (Telepocalypse) fit in very well:
SIP. Abbrev. Standard Initiation Protocol. A meta-technology designed to inspire people to create new, proprietary and competing standards and implementations containing subtle incompatibilities.
VoIP. Very Old Idea Phone. A revolutionary way of extending Bell’s original vision for the telephone, allowing you to dial with a mouse click as well a touchtone keypad and rotary dial.
IMS. Internet Monetisation System. A minor adjustment to Internet Protocol to add a “price” field to packet headers. Earlier versions referred to Innovation Minimisation System. This usage is now deprecated. (Expected release Q2 2012, not available in all markets, check with your service provider in case of sudden loss of unmediated connectivity.)
E911. Slang. Emergency! 911. Whenever an incumbent telco feels chest pain, hot flushes, and sudden loss of wealth, they should call their local political office and declare an “Emergency 911”. (A tax-deductible campaign donation of the usual $911,000 is also expected in return for rescue service.)
ATA. Auntie’s Telephone Adapter. Gives your desk phone a thicker, less flexible “Ethernet” cord and and weighted anchor to stop your clumsy aunt knocking it onto the floor again.
SBC. Archaic. Session Border Confuser. System designed to prevent Skype users in different corporations from being able to talk to one another. No longer in common use.
Report on IETF ENUM WG in German
ENUM soll fuer Telcos tauglich werden
Saturday, August 06, 2005
IETF #63 Carrier ENUM and VoIP Peering
The week was really very tensing, because the suspension was building up during the whole week, to be finally resolved in the last meeting and here at the end, when Carrier ENUM was scheduled. I was originally not very happy to see ENUM scheduled on Friday, but looking backwards it was a very good idea to have it after the VOIP peering and Interconnection BoF.
The VoIP Peering and Interconnect BoF was very interesting, especially the presentations given showed a wide spectrum of opinions and that a lot of basic work needs to done, e.g. clear definitions, defining a scope and scenarios and a requirements document. I will report on the voipeer BoF in detail in a later entry. One of the clear outcomes was that there is a definite need for Carrier ENUM, stated in many presentations, and this paved the way for the discussion in the ENUM WG on this topic.
So the first important decision regarding Carrier ENUM was the overwhelming hum on the question if Carrier ENUM is within the scope of the IETF ENUM WG - there where NO objections. This answered also the question I posted twice on the mailing list to the responsible AD Allison Mankin (who was BTW NOT present at the meeting). Remark: this was somehow prejudged already by adoption of the I-D on Enumservice npd:tel as WG item. This Enumservice is basically aimed for carrier use.
This decision will be reflected in an update of the WG charter and the requirements for Carrier ENUM will be continued to be incorporated in the requirements I-D, requested by Patrik and collected in a hurry by Steve Lind (to be made available officially after the blackout). This I-D was also adopted as WG item. The outcome of the requirements will help to decide if Carrier ENUM can either be incorporated as update to RFC 3761 or in a new RFC. This incorporation in an RFC has been requested by many vendors, because most of their customers demand it.
It was clearly stated by the WG chairs that the data in Carrier ENUM will be available in the public DNS (with no access restrictions), but this does not imply (as usual) that one may access the servers where the URIs may point to without restrictions. Since Carrier ENUM only makes sense if the carriers may enter ALL the numbers they host into Carrier ENUM (carrier opt-in and not user opt-in), this automatically implies for the requirements that the carriers must protect the privacy of their customers, e.g. by entering only URIs pointing to their network such as sip:+xxxxxxx@provider.net and eventually rolling out the whole block of numbers to give no information of numbers in-service.
Since David Meyer from voippeer was also available at the meeting, the opportunity was taken to define a clear split of responsibilites and scope between ENUM WG and a potential voipeer WG: these access restriction and eventual peering agreements are definitely within the scope of voipeer, the ENUM WG is responsible for the DNS related issues e.g. the implementation of Carrier ENUM in the DNS and required ENUMservices.
Having set these basic principles aside, the discussion moved on to the "details": where to place Carrier ENUM in the DNS?
Two proposals where brought forward as I-Ds:
- the usage of non-terminal NAPTRs to split User and Carrier e.g. in Tier 1 or below by Steve Lind and Penn Pfautz
- and the proposal from Michael Haberler and myself to split of the carrier tree somewhere below e164.arpa.
The usage of non-terminal NAPTRs and the problems caused by this e.g. for countries with numbering plans using variable number lenght has been already discussed at lenght on the ENUM mailing list. The usage of non-terminal NAPTRs will also require a fix in the DDDS application and also in RFC3761, as already pointed ot by Lawrence in his I-D modest proposal. This will be done in any case.
Penn Pfautz requested a (non-binding) hum on the opinion of the partizipants regarding the general directions of the future discussions and the chairs posed the following questions to the audience:
Do you prefer for implementation of Carrier ENUM:
A. with non-terminals
B. a split-off (to be decided where) in e164.arpa
C. a completely new tree for Carrier ENUM
Result was surprisingly clear, no hums for A. and C., an overwhelming hum for B.
Regarding option B. basically two sub-options exist:
- splitting the tree immediately below e164.arpa, by using e.g. c.e164.arpa as apex.
This is of course the most straightforward solution, and would require in principle only some additional lines in an updated RFC3761, but wouldl require heavy involvement of the IAB, RIPE and especially the ITU-T, basically a re-run of the (still not finalized) discussion regarding the Interim Procedures.
- leaving the point of split-off to the national entity responsible for "cc" .e164.arpa and indicate the split level used within this country code within the DNS itself, e.g. c."cc".e164.arpa. The split-off point could be after 0-n digits. This proposal is not as straight-forward as the first, but the complication would only concern carreir clients, would leave the ITU-T interim procedures untouched and could be implemented in countries willing to do so immediately. It could also cause some more pressure on national regulators by carriers to opt-in into e164.arpa or to go commercial.
The next steps will be:
- move the requirements I-D forward as fast as possible via mailing-list discussion
- a solution should be finalized latest at the next IETF in Vancouver (November)
- this is especially necessary if the solution requires input to the ITU-T
- the next ITU-T SG2 Plenary is in December 2005
Note for TISPAN: this decisions have important implications to the current work of TISPAN WG4 (and eventually also for the plans of GSMA using Carrier ENUM within GRX)
TISPAN WG4 will discuss these issues at the next ad-hoc meeting end of August in London to provide a proposal for a common position of TISPAN for the next TISPAN Plenary in September 2005.
The rest of the ENUM WG for completeness:
ENUM Implementation Issues and Experiences will go to WGLC.
IANA Registration for Enumservice Voice (the vovi minus video), only containing voice:tel will be a WG item (finally).
IANA Registration for ENUMservice Mobile Webpage caused already some discussion on the mailing list and also within the meeting. James Seng raised an issue and comments this on his blog:
... I think I surprised quite a few people when I stood up and objected to Shin's mobileweb registration (basically, a ENUMservice for mobile web). Now, Shin is a close friend but I think it is a bad idea to start putting session negiotation information into ENUM. Its a slippery slope to go near there - DNS should remains as DNS - you throw something at it and it give you back something. The capability negiotation should be done within the session setup, and especially HTTP already provides User-Agent negiotation that serves the need
I can understand why mobileweb would make sense - It is very helpful for a registry/registrar who can start to market a new product ("register your mobile web address now!") but lets not taint the protocol.
Some people also raised concerns in filling up the DNS and especially the responses with too many NAPTRs.
Jon Peterson stood up in his position as AD and stated that this problem is recurring (we had it already with voice:sip) and should basically not discussed again and again with specific applications, but discussed in general and solved.
The rest of the meeting concerned IRIS EREG, and the I-Ds on validation (an alpine co-operation ;-) are also moving slowly forward:
ENUM Validation Architecture
ENUM Validation Token Format Definition
ENUM Validation Information Mapping for the Extensible Provisioning Protocol
the documents have also been approved as WG items.



